Search results for tag #unix
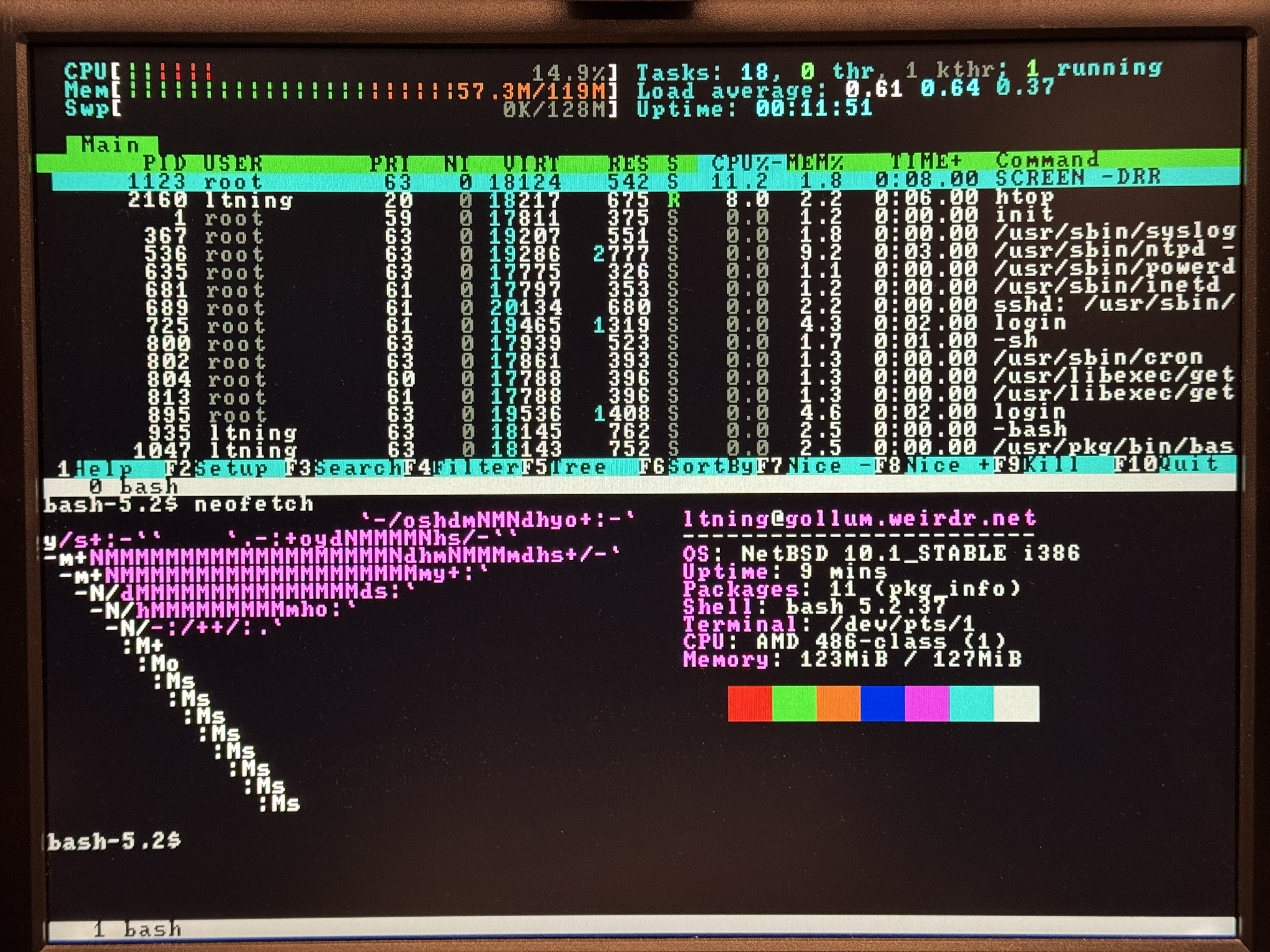
All of those things are absolutely wonderful and make many of todays software developers look ... spoiled? What I want, however - and what I love doing - is making this old hardware do stuff its makers never dreamt of, things that are as far removed from their time as possible. That's why I will, if #NetBSD permits, run bleeding edge BSD on a 286-on-486steroids, and why I run web+ftp+irc servers (yes, multitaskign) on one 286 and multiple BBS nodes on a 386 - like one used to do, of course.
I cannot state often enough how amazing it is that there's still software developed today that will work under such constraints.
![[?]](https://weirdr.net/snac/ltning/s/271784d3d55493d08c915e5bb7862aaf.jpeg)